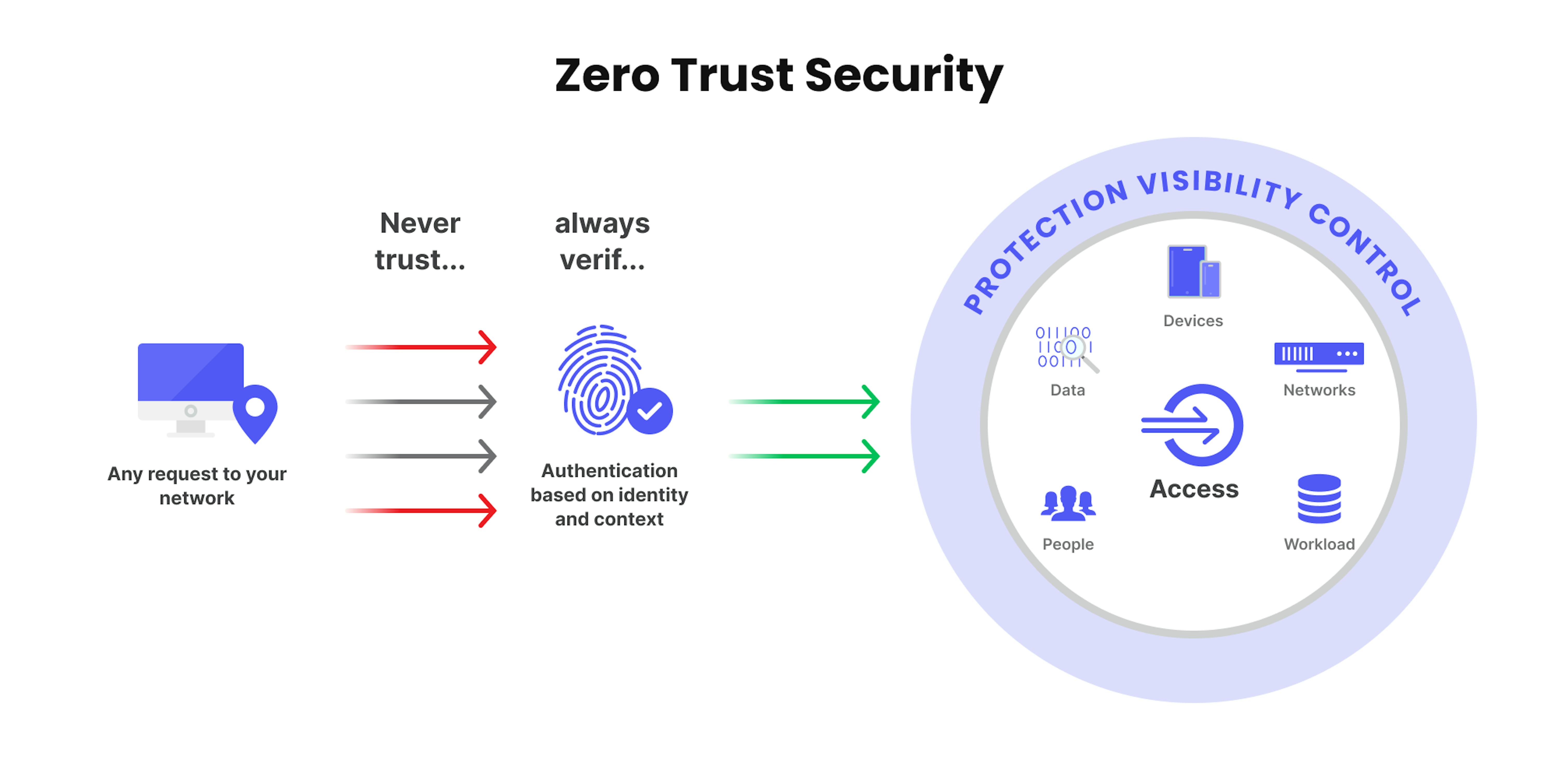
Zero Trust Architecture (ZTA) is a type of cybersecurity model that believes in the "never trust, always verify" principle. It assumes no user, device, or system is inherently trusted inside or outside the organization's network. In fact, it enforces strict access controls, continuous authentication, and monitoring for every interaction.
How Zero Trust Works
Verify Identity
Users and devices must authenticate at each access point using methods like MFA.
Enforce Least Privilege Access:
Access is granted only to resources necessary for the user or device's task, thereby minimizing over-privileged access.
Continuous Monitoring:
Activity is constantly analyzed for suspicious behavior using tools like User and Entity Behavior Analytics (UEBA) or Security Information and Event Management (SIEM).
Micro-Segmentation:
The network is divided into smaller segments to isolate resources, thereby limiting lateral movement in case of a breach.
Dynamic Risk-Based Policies:
Access decisions are also made in real-time using device health, geolocation, user behavior, and the sensitivity of the data accessed.
Encryption and Secure Communication:
Data is encrypted as it travels over public networks and it remains encrypted even when it's stored.
Key Technologies in ZTA
Identity and Access Management (IAM): Robust user authentication
Zero Trust Network Access (ZTNA): Contextual based access to applications.
Endpoint Security: Verifies the health and security posture of devices.
Data Loss Prevention (DLP): It monitors and protects sensitive information.
Benefits of ZTA
Better Security: It reduces the attack surface by assuming all users and devices are untrusted.
Better Incident Response: Continuous monitoring improves detection and response to threats.
Protection for Remote Work: Ensures secure access regardless of location or device.
Data Protection: Strict access controls and encryption safeguard sensitive information.
How Zero Trust Works
Verify Identity
Users and devices must authenticate at each access point using methods like MFA.
Enforce Least Privilege Access:
Access is granted only to resources necessary for the user or device's task, thereby minimizing over-privileged access.
Continuous Monitoring:
Activity is constantly analyzed for suspicious behavior using tools like User and Entity Behavior Analytics (UEBA) or Security Information and Event Management (SIEM).
Micro-Segmentation:
The network is divided into smaller segments to isolate resources, thereby limiting lateral movement in case of a breach.
Dynamic Risk-Based Policies:
Access decisions are also made in real-time using device health, geolocation, user behavior, and the sensitivity of the data accessed.
Encryption and Secure Communication:
Data is encrypted as it travels over public networks and it remains encrypted even when it's stored.
Key Technologies in ZTA
Identity and Access Management (IAM): Robust user authentication
Zero Trust Network Access (ZTNA): Contextual based access to applications.
Endpoint Security: Verifies the health and security posture of devices.
Data Loss Prevention (DLP): It monitors and protects sensitive information.
Benefits of ZTA
Better Security: It reduces the attack surface by assuming all users and devices are untrusted.
Better Incident Response: Continuous monitoring improves detection and response to threats.
Protection for Remote Work: Ensures secure access regardless of location or device.
Data Protection: Strict access controls and encryption safeguard sensitive information.

No comments:
Post a Comment