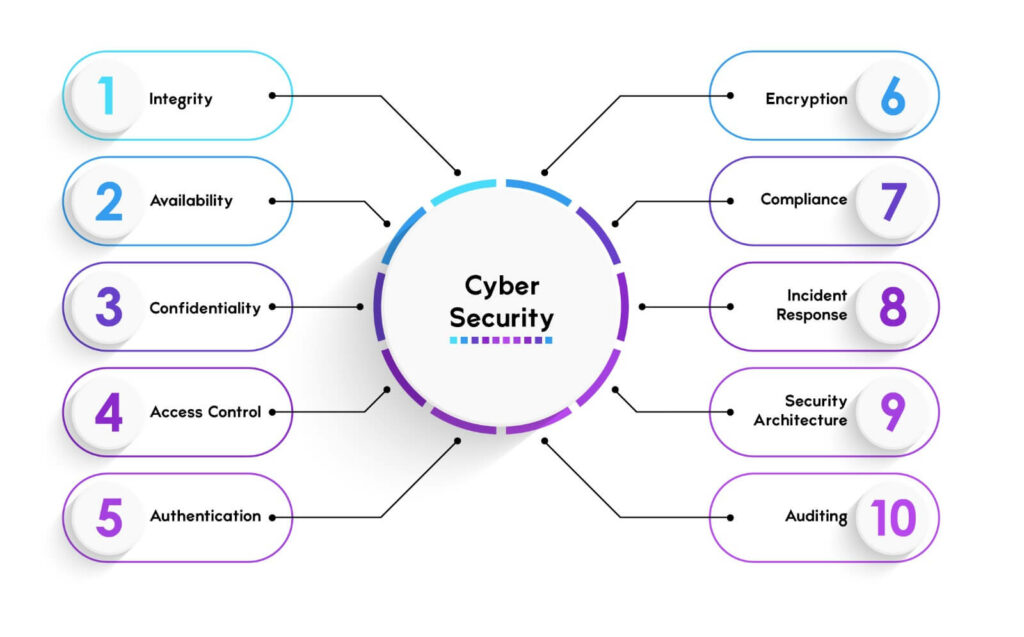
Cybersecurity in the social media site stands at the forefront of protecting the private information of users, digital privacy, and online safety. In this modern age where networks such as Facebook, Instagram, Twitter, TikTok, and LinkedIn are widely used to share personal information, someone needs to understand how security attacks may be posed through such exposures. A few of the key security issues have been highlighted below as individuals and organizations can improve their own safety.
1. Risks associated with Privacy and Data Protection:
Leaked Personal Data: The social networking sites collect immense personal data, including location, interests, contact, and photographs. All these data, unless properly secured, will be misused for evil.
Data Breaches: Large social media companies are frequent victims of cyberattacks, and the result could be that personal information of users will be prone to breach. Try using strong, unique passwords for your account and enable two-factor authentication (2FA).
Third-Party Apps: Many social media services permit third-party applications to access users' data. These apps may be vulnerable to hacks or exploit permissions granted by users. It's very important to check the permissions granted to such apps and delete any that are unnecessary or suspicious.
2. Phishing and Scams:
Phishing Attack: Cybercriminals often use social media to conduct phishing attacks, portraying either a friend, brand, or company pretending to request sensitive information, such as passwords, credit card numbers, or login credentials.
Scam Links: There are messages or posts with links to fake sites designed to steal personal information. These often appear authentic but are crafted to deceive.
3. Hacking and Account Takeover:
Account Hijacking: This is the hacking of social media accounts using weak passwords, social engineering, or phishing. Through hacking, an attacker can take over the account to spread malware, commit fraud, or steal more personal data.
Credential Stuffing: Cybercriminals can try using leaked passwords from other breaches to access users' social media accounts if such users reuse the same password on another site. It is, therefore, important that each site should have its own unique password.
4. Malware and Ransomware:
Malicious Links: Malware and viruses are most times spread through social media. Caution should always be taken on unknown sources' links or attachments because these links will also lead to malware infections.
Ransomware: Hackers have used social media to target users with ransomware, locking them out of their accounts until ransom is paid. This seems to be more common in business-related social media attacks.
5. Social Engineering and Impersonation:
Impersonation: Hackers may impersonate legitimate accounts or use fake profiles to manipulate users into revealing sensitive information or participating in fraudulent schemes.
Exploiting Trust: Social engineers use psychological manipulation to deceive users into revealing confidential information. For example, a scammer may create a fake customer support account to gain trust and ask for sensitive data.
6. Best Practices for Cybersecurity on Social Media:
Use Strong, Unique Passwords: Use complex passwords and avoid reusing them across multiple accounts. Consider using a password manager to keep track of different credentials.
Enable Two-Factor Authentication (2FA): Check Privacy Settings: Regularly check the privacy settings of your accounts. Restrict access to your posts and information only to friends or followers whom you can fully trust.
Be Careful with Links and Attachments: Be wary of clicking on suspicious links or downloading attachments, especially when they appear to come from a known sender.
Educate Yourself on Phishing: Learn to recognize phishing attempts, such as fake login pages or messages that create a sense of urgency.
Monitor Accounts for Suspicious Activity: Keep on the lookout for any unauthorized activity or unfamiliar devices logged into your accounts.
Report Suspicious Activity: If you notice any suspicious accounts or activity on your social media profiles, report it to the platform administrators right away.
7. Legal and Compliance Issues:
GDPR and Data Protection: Social media sites have to comply with the laws like General Data Protection Regulation (GDPR) in Europe, which ensures transparency and user's consent for further data collection and sharing. Be aware of your rights and privacy settings subject to such regulations.
Digital Footprint: Anything posted or shared online through social media contributes to your digital footprint. That includes posts, photos, location data, likes, and comments. All this can be manipulated if it falls into the wrong hands.
8. Cybersecurity for Social Media Managers and Businesses:
Social Media Account Security: Most of the businesses use this media for customer engagement, marketing, and brand presence. Security of accounts is very crucial so that the reputation of a brand or customer will not get damaged. Use secure log-in methods and train the staff on account security.
Secure Communication: In case information is communicated through social media channels either to customers or staff members, keep the same encrypted in order not to intercept the data.
Regular Security Audits: Companies should periodically audit their presence in social media and the applications they use for insecurity issues and compare them with standard guidelines set for security.
Conclusion
The origin and evolution of social media have brought along both risks and opportunities related to cybersecurity. By observing one's personal security settings, identifying threats as phishing and scams, and following best data protection practices, users can ease risks associated with social media usage.